

-
Posted by Sceptre
- 02/04/2022
Discover Devices On Your Network
In this article you will learn how to discover devices on your network with Netdiscover and Python on Kali Linux. Perhaps your internet is slower than usual or you are your wifi connection is constantly dropping. Maybe you never changed your default password and your neighbours are watching netflix on your wifi. Whatever the reason we will find any intruders on our network with a few easy steps.
First things first, fire up Kali and attach your wireless adapter. I have shown how to do this in setting up a virtual lab.
Secondly, you will need to connect your wireless adapter to your wifi network. If you go to the top right corner of Kali you should see drop down options to connect to a wifi network. You can find Select Network option in the top right corner of your Kali Machine. This may look different depending on what image of Kali you are using. Input the wifi password and now Kali should be connected to the wifi.
ifconfig in our terminal we should be able to see that our wireless adapter wlan0 now has been assigned its own IP address 192.168.0.21 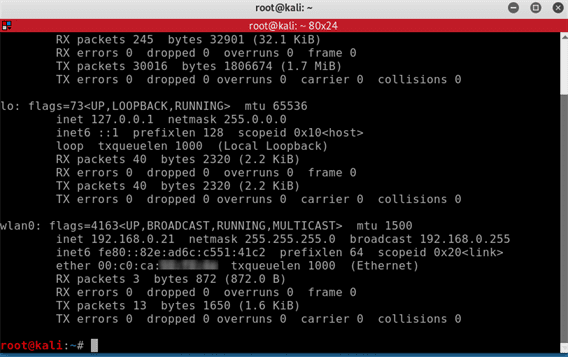
netdiscover --help 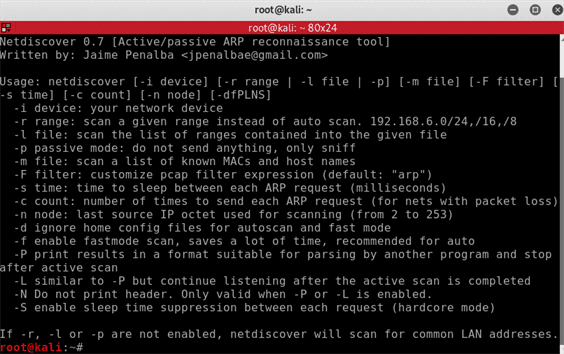
OK as you can see Netdiscover gives us plenty of options to scan including passive mode and being able to print the results to a file.
For now we will just use the [-i device] and [-r range] options for a quick scan on our home network.
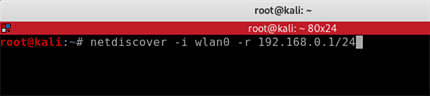
Using the IP of the wireless adapter (mine is 192.168.0.21) we will command Netdiscover to scan the entire range of subnet on this network. It will broadcast request packets to every IP on the subnet from 1 to 254 asking ‘are you there’ and if there is a reply it will be ‘yes I am, this is my mac address’.
netdiscover -i wlan0 -r 192.168.0.1/24By appending 1/24 to the end of the IP address, Netdiscover will know to scan all subnets from 1 to 254.
Here are the results of the Netdiscover Scan results of my home network.
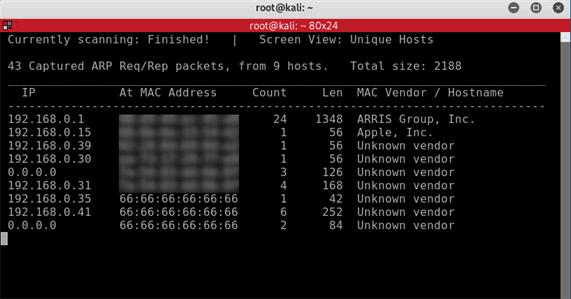
The top results are my router, my Apple device and a few other wireless machines that I am able to recognise by their MAC address. However there is a Mac Address that I do not recognise 66:66:66:66:66:66. Obviously this is a very suspicious Mac address as all Mac’s begin with 00 and I need to secure my home network.
Scanning The Network With Python
Python has a very useful module for sending and receiving ARP packets called Scapy. Scapy has a function ARP Ping that will do all the work to scan the network and return the IP addresses, Mac addresses and Mac Vendor’s name on the same network. All you have to do is add the IP address that you want to scan to this Python Script.
#!/usr/bin/env python
import scapy.all as scapy
def scan(ip):
arp_request = scapy.ARP() #arp packet made by scapy
print(arp_request.summary())
scan("192.168.19.26/24")
ARP Ping is really a great tool to scan the network but maybe you would like to build your own scanner so that you can customise it how you like. In this next Python script I have made another network scanner using Scapy without the ARP Ping function. This script will find your gateway IP on your computer and then send the ARP packets to return an answer from devices on the same network with their IP address and MAC address. The only difference is you will not have to add the IP you want to scan as the program will find your gateway IP using subprocess and regular expression modules.
Additionally I have added an API to retrieve the data of the Mac Vendors name from Mac address.io If the API key in the script is no longer working you can go to macaddress.io to obtain a new API key and replace it with mine in the script.
#!/usr/bin/env python
import scapy.all as scapy
import subprocess
import re
import maclookup
from maclookup import ApiClient
import logging
# 1. pip install maclookup
# 2. python3 sceptrescan.py
# 3. if ApiClient out of use, please get
# new ApiClient https://macaddress.io/
client = ApiClient('at_QY6om50bspgqg83KBf0fDHDaHbiRC')
#function to find gateway IP using subprocess and regex
def get_gateway():
get_route = subprocess.check_output(["ip route"], shell=True)
gateway_result = re.search(r"(25[0-5]|2[0-4][0-9]|[01]?[0-9][0-9]?)\.(25[0-5]|2[0-4][0-9]|[01]?[0-9][0-9]?)\.(25[0-5]\
|2[0-4][0-9]|[01]?[0-9][0-9]?)\.(25[0-5]|2[0-4][0-9]|[01]?[0-9][0-9]?)", str(get_route))
return gateway_result.group(0)
def scan(ip):
arp_request = scapy.ARP(pdst=ip) #create arp packet
broadcast = scapy.Ether(dst="ff:ff:ff:ff:ff:ff")#direct to mac address
arp_request_broadcast = broadcast/arp_request #join packets
answered_list = scapy.srp(arp_request_broadcast, timeout=1, verbose=False)[0] #send and receive function
clients_list = []
for element in answered_list:
client_dict = {"ip":element[1].psrc, "mac": element[1].hwsrc}
mac_vendor = client.get_vendor(client_dict["mac"])
macmac = {"macvendor":mac_vendor}
client_dict.update(macmac)
clients_list.append(client_dict)
return clients_list
def print_result(results_list):
print("IP\t\tAt MAC Address\t Vendor Name")
print("------------------------------------------------")
for client in results_list:
print(client["ip"] + "\t" + client["mac"], client["macvendor"] )
#get gateway ip and add subnet
gateway = get_gateway()
gateway = (gateway + "/24")
print("Scanning Gateway Address " + gateway + " for network clients")
scan_result = scan(gateway)
print_result(scan_result)
If you found this blog useful to “discover devices on your network”, please share it in social media channels to help others learn and do not forget to follow me on Twitter for latest blog updates. Peace.





