

-
Posted by Sceptre
- 09/04/2022
Starting With The Man In The Middle
In this article you will learn how to perform a Man in the Middle attack. There are differents to do a MitM attack including DNS and HTTPS spoofing however we will be looking at ARP spoofing. We will cover the theory and then I will demonstrate ARP spoofing on a target windows machine.
What is a Man in the Middle attack?
Man in the middle attacks occur when a hacker positions them self between the target and their host or another target. A hacker is able to intercept network traffic or communications in order to spy on the victim, steal information or gain access to a device.
For example, an attacker can join a public wifi in a coffee shop and with a few easy commands can route the wireless traffic the customers through the attackers laptop. Usernames, passwords, images and sensitive information can be viewed in real time and also saved on to a file for the attacker to review later.
What is ARP?
Address Resolution Protocol (ARP) allows devices to connect to eachother over a network by their MAC addresses. The way that it works is that a device sends a message out to all the other devices on the same network asking ‘does anyone have this IP address?’. This message is sent out as an ARP packet. If any of the other devices on the network have the IP address they will respond ‘I have that IP address, my MAC address is ……..’. This message is received and the IP and Mac addresses are now linked together on the computers ARP table. The devices can communicate with eachother.
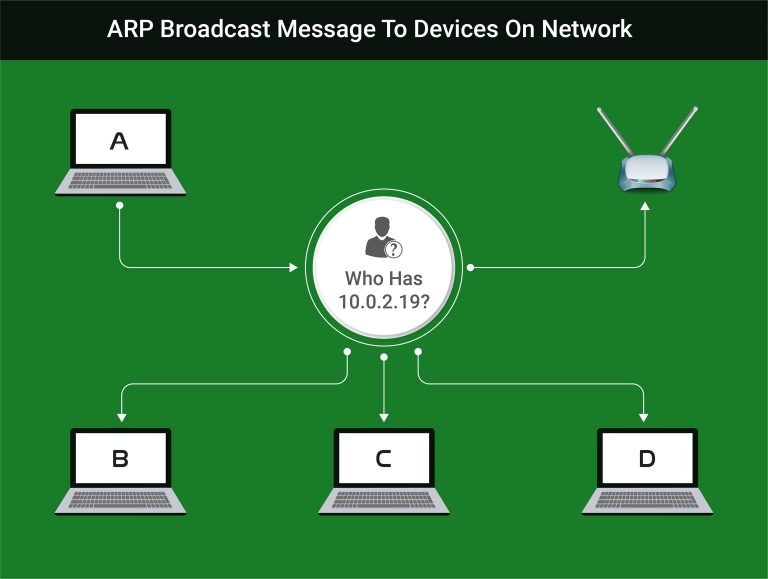
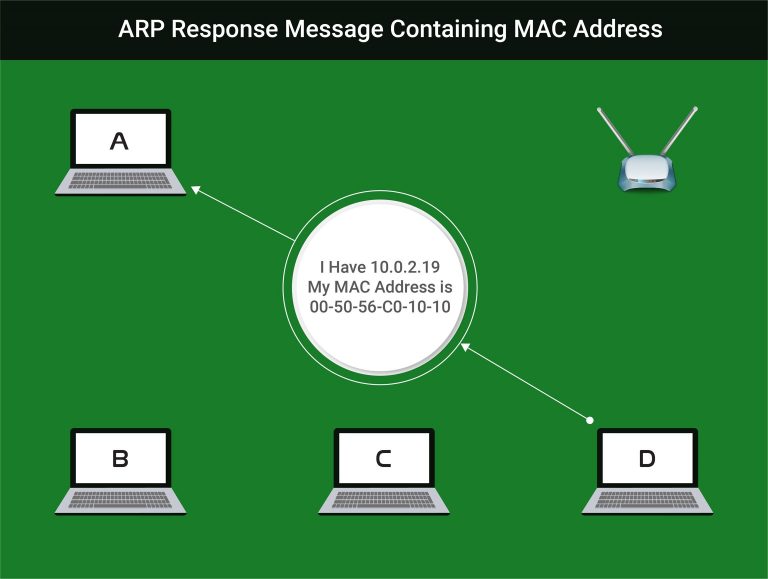
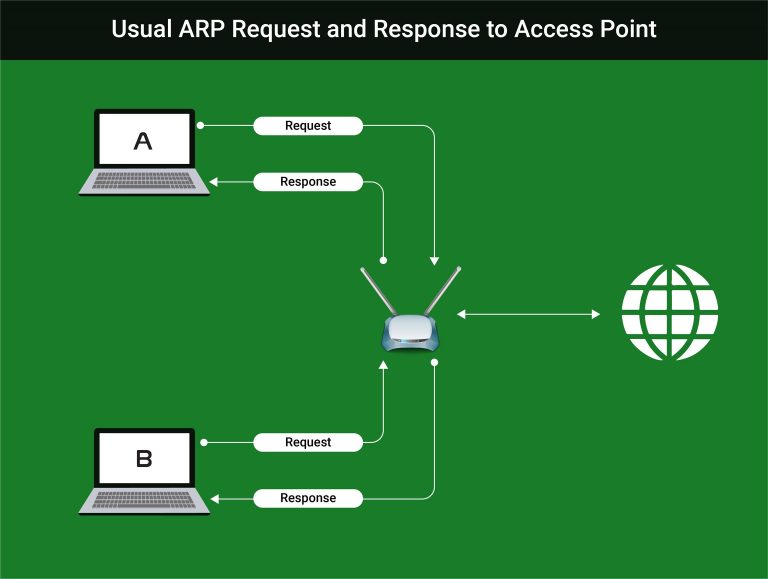
When any device wants to use the internet, a request is sent to the router (access point), the router sends the request to the internet and then sends the response back to the device. This is the usual way that a hacker and a victim or anyone else communicates with the internet.
During ARP Spoofing the targets requests are sent to the hackers machine instead of the access point. The hacker’s device then forwards the request to the access point and then forwards the response back to the target. In this position all traffic from the target machine is flowing through the hackers computer.
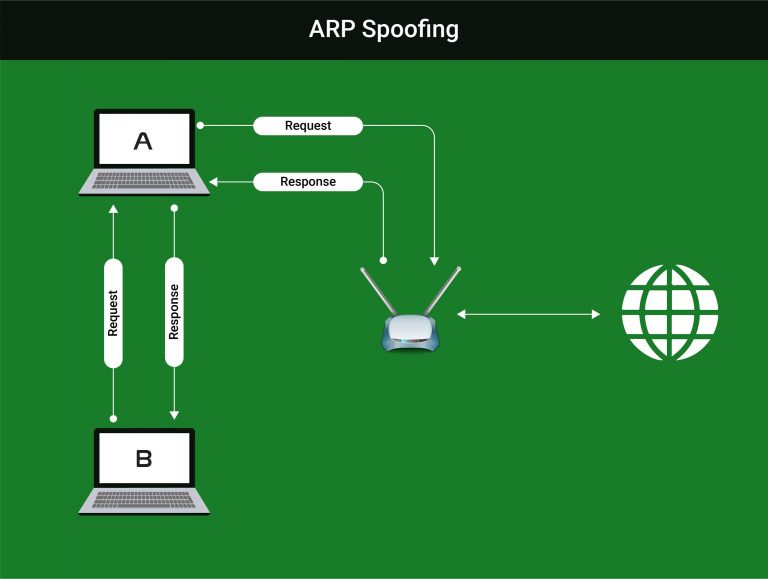
So how is this possible? The hacker sends a manipulated ARP response packet to the access point claiming to be the IP address of the target machine. The access point then updates its ARP table to link the IP address with the MAC address of the hacker.
The same method takes place with the victim machine, by the hacker sending a forged ARP response pretending to be the IP address of the access point. The victim device will update its ARP table to associate the hackers MAC address with the router’s IP address. Any requests from the victim’s machine will be sent directly to the router.
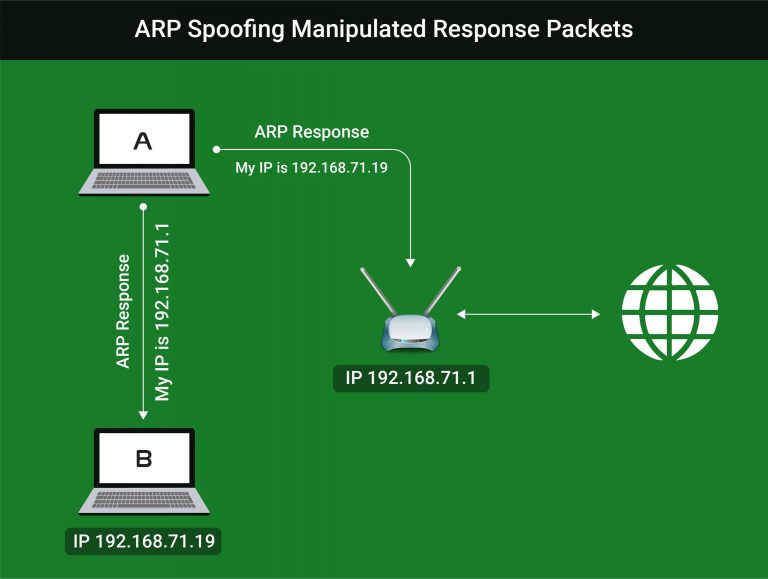
How To Perfom ARP Spoof
There are a number of ways and tools to become in the Man in the Middle, for now we will use a tool called ARP Spoof which is built into Kali Linux.
Firstly, to run this attack against real targets, you will need to join a wifi network. Connect your wireless adapter , in the top right corner of Kali select the drop down option to connect to a wifi network and input the wifi password if required.
Type ifconfig in the terminal to see the wireless adapter wlan0 has been assigned an IP address, mine is 192.168.0.21
All we need now are the IP addresses of the gateway and the target machine.
We can get the gateway IP in Kali by typing arp -a .
arp -a to show the ARP table . 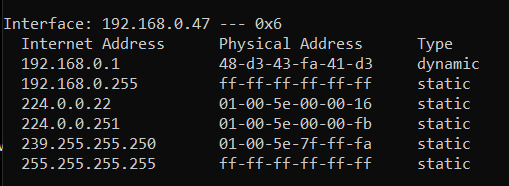
Now that we have the IP addresses we can run the following commands in the Kali terminal.
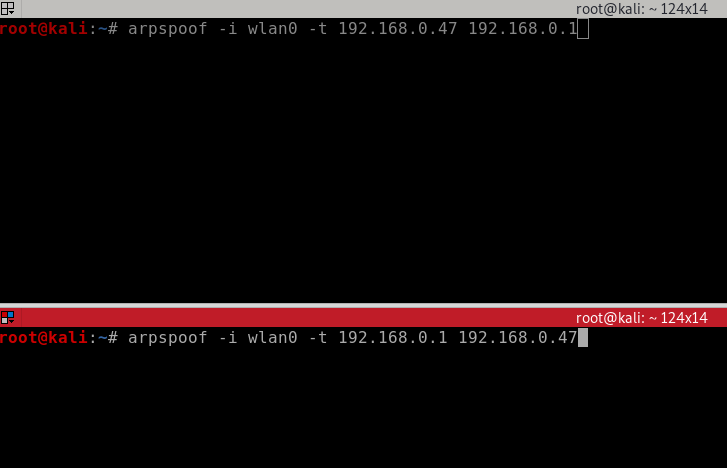
The first command will deceive the Windows target machine into thinking that I am the router.
arpspoof -i [interface] -t [target IP] [gateway IP]
arpspoof -i wlan0 -t 192.168.0.47 192.168.0.1
The second command will deceive the router machine into thinking that I am the target Windows machine.
arpspoof -i [interface] -t [gateway IP] [target IP]
arpspoof -i wlan0 -t 192.168.0.1 192.168.0.47
Once you have these 2 commands in the split window terminal, hit Enter on both of them and you should see the arp replys on both Kali terminals. If we take a look again at the Windows ARP Table, we will notice that the router (access point) MAC address has been changed and updated to the same MAC address of my attacking machine 00-c0-ca-99-38-4f. and it thinks that I am the router. Therefore all requests to the internet will flow through my machine.
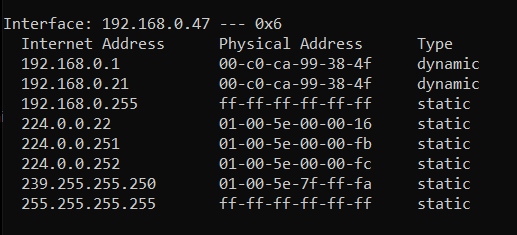
As you can see in the Windows ARP table above, there are 2 IP addresses with the same MAC addresses. As MAC addresses are unique this is really suspicious and it can be a way of detecting MitM attacks.
So now any requests from the Windows machine will be sent to our attacking machine but they will stop there. The attacking machine is not actually a router so we all have to do is to set up ip forwarding so that we can forward the requests to the router.
Whilst arpspoof is running in the split terminal windows, split the terminal one more time so that you now have 3 terminal windows. In the 3rd window enter the following command.
echo 1>/proc/sys/net/ipv4/ip_forward
So with 3 simple commands we have positioned ourselves to be the Man in the Middle. Any requests to the internet from the target machine will flow through our computer. The only issue now is that we can not read the packets of data that are being sent. We can store them as a file to open up and analyse in Wireshark but before we do that, lets look at another Kali Linux tool to become the Man in the Middle.
This blog is still on progress and will be completed soon.
Please follow me on Twitter for blog updates. Thank you





